Based on current trends, I believe the top two HSM modules for developers in 2025 will combine robust security features, high reliability, and easy integration options. Modules supporting advanced interfaces like PCIe Gen5 and cloud multi-tenancy will be essential. They should also handle larger keys and workloads for future-proofing. If you keep exploring, you’ll uncover the key factors to contemplate for choosing these leading solutions and how they fit into evolving security needs.
Key Takeaways
- Prioritize modules supporting future interface standards like PCIe Gen4/Gen5 for sustained high performance.
- Choose HSMs with modular architectures enabling seamless hardware upgrades and scalability.
- Ensure compatibility with cloud environments and multi-tenancy features for flexible deployment.
- Opt for modules with robust security features, including hardware encryption and tamper resistance.
- Select solutions capable of handling larger keys and increased cryptographic workloads to meet evolving security demands.
Python Programming for Beginners: Updated Guide to Coding Mastery

Are you a beginner enthusiastic to master coding quickly? “Python Programming for Beginners: Updated Guide to Coding Mastery” is ideal if you want straightforward, step-by-step instructions that blend theory with practical exercises. I found it perfect for starting my journey, thanks to clear explanations and easy-to-follow projects. It covers fundamental topics like algorithms, flowcharts, pseudocode, and Python basics, making complex ideas accessible. The book’s practical focus on integrating Python with Arduino and Raspberry Pi projects really helped me apply what I learned. Even as a newcomer, I appreciated its simplicity and engaging content, making my first coding experience enjoyable and effective.
Best For: Beginners seeking a straightforward, practical introduction to Python programming and related projects, especially those interested in integrating Python with Arduino and Raspberry Pi.
Pros:
- Clear, step-by-step instructions that make complex topics accessible for newcomers
- Includes practical projects and exercises to reinforce learning and application
- Well-suited for hobbyists and enthusiasts with little to no prior programming experience
Cons:
- Some readers may find the coverage too basic, especially regarding fundamental concepts like algorithms and pseudocode
- The book may lack depth for those seeking more advanced or comprehensive programming knowledge
- Limited information on troubleshooting or more complex project integration aspects
M.2 to SATA3.0 Adapter Card
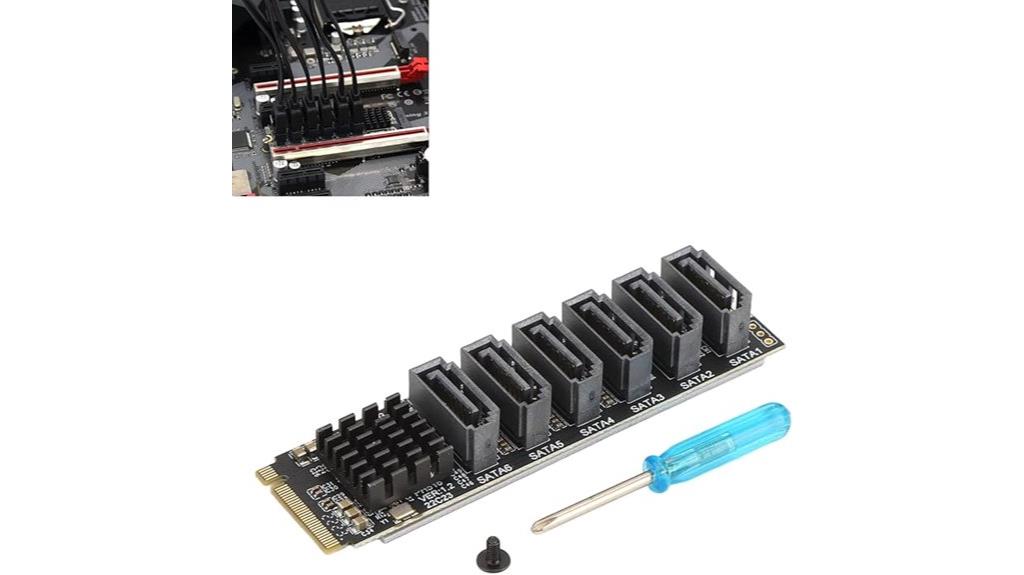
The M.2 to SATA3.0 Adapter Card is an ideal choice for developers and IT professionals who need to expand storage capacity quickly and reliably. It supports 6Gbps data transfer, converting M.2 to SATA3.0 with five downstream ports, making it perfect for multiple device connections. Powered by the ASM1166 chip, it guarantees stable, high-speed performance. Its plug-and-play design simplifies installation, and the built-in heat sink maintains thermal stability. Compatible with Windows, macOS, and Linux, this adapter is suitable for desktops and servers, providing a solid, efficient solution for expanding storage without complicated setup or performance issues.
Best For: IT professionals and developers seeking a reliable, high-speed M.2 to SATA expansion solution for desktops or servers.
Pros:
- Supports 6Gbps high-speed data transfer with five downstream SATA ports.
- Compatible with Windows, macOS, and Linux, ensuring broad OS support.
- Plug-and-play design with integrated heat sink for easy installation and thermal stability.
Cons:
- Customer ratings are moderate, with a 3.1 out of 5 stars based on reviews.
- Pricing and availability may vary; potential for additional costs or fees.
- Limited detailed warranty information and support options available upfront.
Factors to Consider When Choosing HSM Modules for Developers

When choosing HSM modules, I focus on compatibility with my devices to guarantee smooth integration. I also weigh security features, performance, and ease of use to meet my project’s needs while keeping costs within budget. Considering these points helps me select the best module for reliable and efficient development.
Compatibility With Devices
Choosing the right HSM module requires careful attention to device compatibility, ensuring it can seamlessly integrate with your hardware setup. First, verify that the module supports your device’s specific hardware interface, whether PCIe, USB, or SPI. It’s also essential to confirm compatibility with your operating system and firmware version to prevent integration issues. Check that the HSM adheres to relevant industry standards and security certifications for your application’s compliance needs. Additionally, review the physical form factor and connection type to match your device’s hardware specifications. Manufacturer documentation is invaluable—consult their supported device lists and compatibility charts to avoid surprises during deployment. Ensuring these factors align guarantees smooth integration and peak performance in your development environment.
Security Features Offered
Security features are a critical aspect to contemplate when selecting HSM modules, as they directly impact the integrity and confidentiality of your cryptographic operations. Hardware-based encryption protects keys from software attacks, ensuring sensitive data remains secure. Many HSMs support secure key generation and storage, preventing key extraction and unauthorized access. Tamper-evident and tamper-resistant designs help detect physical breaches, enabling rapid response. Some modules include secure boot and firmware validation to block malicious code execution. Compliance with industry standards like FIPS 140-2 or Common Criteria demonstrates a high level of trustworthiness and security assurance. These features collectively ensure your cryptographic environment remains resilient against evolving threats, making security a non-negotiable factor when choosing the right HSM module.
Performance and Speed
Performance and speed are key considerations when selecting HSM modules, as they directly impact how quickly and efficiently cryptographic operations can be performed. The cryptographic throughput varies widely, from thousands to millions of operations per second, depending on hardware design. Factors like clock frequency, core count, and internal architecture determine processing power, with high-speed modules supporting multiple concurrent operations to reduce latency and boost transaction throughput. The interface type also matters; PCIe-based modules offer higher data transfer rates compared to USB or network interfaces, enabling faster communication. Additionally, efficient data handling and optimized firmware can markedly enhance real-world speed, ensuring rapid response times during cryptographic tasks. Prioritizing these performance factors helps achieve a seamless balance between speed and reliability in your security infrastructure.
Integration Ease
Seamless integration is crucial when selecting HSM modules, as it can markedly reduce development time and prevent compatibility issues. I look for modules that offer APIs, SDKs, or standard interfaces like PKCS#11, Microsoft CNG, or Java JCE, ensuring smooth compatibility with my development environment. Extensive documentation and robust support resources are essential, making integration straightforward and troubleshooting easier. I also consider whether the HSM supports plug-and-play functionality or needs extensive configuration, which impacts deployment speed. Additionally, I evaluate how much hardware and software customization is required, as minimal adjustments help streamline the process. Ultimately, an HSM module with easy integration options allows me to focus on core development tasks and accelerates project timelines.
Cost and Budget
Choosing the right HSM module also involves carefully considering the cost and how it fits within my budget. HSM prices can vary widely, from a few hundred to several thousand dollars, depending on features and security levels. If I have budget constraints, I might opt for basic models that cover essential security needs but lack advanced cryptographic functions or easy integration options. However, investing in a higher-priced module often offers better performance, scalability, and long-term value, especially for enterprise applications. It’s also important to factor in the total cost of ownership, including maintenance, licensing, and support fees, not just the initial purchase. Striking a balance between affordability and security is key to ensuring the HSM module meets both my financial and compliance requirements.
Future Scalability
As security needs grow, guaranteeing that an HSM module can support future scalability becomes essential. I look for modules that can handle increasing cryptographic workloads and larger key sizes as security standards evolve. Modular architectures are a plus, allowing seamless hardware upgrades and expansion to keep pace with technological advances. Compatibility with emerging interfaces like PCIe Gen4 or Gen5 ensures high performance remains intact in future environments. For cloud deployment, I prioritize HSMs that support multi-tenancy and align with evolving security standards. Planning for scalability also means evaluating the module’s capacity to manage higher transaction volumes and more concurrent operations over time. By considering these factors, I can select HSM modules that adapt to future demands without compromising security or performance.
Frequently Asked Questions
How Do HSM Modules Ensure Compliance With Global Security Standards?
HSM modules guarantee compliance with global security standards by implementing strict cryptographic protocols and adhering to industry regulations like FIPS 140-2 and PCI DSS. I verify that the modules are certified and regularly updated to meet evolving standards. They also incorporate secure key management practices, audit logging, and tamper resistance, giving me confidence that my data stays protected and compliant across different jurisdictions and use cases.
What Are the Key Integration Challenges With HSM Modules in Existing Systems?
Think of integrating HSM modules like fitting a new gear into a complex machine—precision matters. The main challenges I face include compatibility issues with legacy systems, ensuring secure key management during integration, and managing latency to keep performance smooth. Sometimes, legacy hardware isn’t designed for these modules, making integration feel like solving a puzzle. Overcoming these hurdles requires careful planning, robust APIs, and thorough testing to keep everything running seamlessly.
How Do Different HSM Modules Compare in Terms of Performance and Cost?
I find that HSM modules vary considerably in performance and cost. High-end modules deliver faster encryption and decryption, ideal for demanding applications, but they come with a higher price tag. Meanwhile, more affordable options still provide solid security, though slightly slower speeds. I recommend evaluating your specific needs — if speed is essential, investing in premium modules pays off; for budget-conscious projects, mid-range options work well.
What Future Trends Are Expected to Influence HSM Module Development?
I believe future trends like increased adoption of AI and blockchain will push HSM development toward even greater security, speed, and scalability. We’ll see more integration with cloud services, making HSMs more accessible for developers. Additionally, advances in quantum-resistant algorithms will be vital for safeguarding data. I’m excited about these innovations, as they’ll make HSM modules more reliable, easier to deploy, and better suited for evolving security needs.
How Can Developers Optimize HSM Module Deployment for Scalability?
To optimize HSM module deployment for scalability, I focus on modular architecture and load balancing. I guarantee my setup can easily add or remove HSMs as demand grows, avoiding bottlenecks. Automating provisioning and monitoring helps me maintain performance and security. I also leverage cloud integration for flexible resource allocation, enabling seamless scaling without compromising compliance or data protection. This approach keeps my system resilient and efficient under increasing workloads.
Conclusion
Choosing the right HSM module is like planting a seed for future growth; it requires careful nurturing and foresight. When I select a module that’s secure, reliable, and easy to integrate, I’m not just safeguarding data—I’m building a foundation that can grow with my needs. Imagine a vault that’s both unbreakable and seamlessly woven into my system, ready to defend my digital assets today and scale effortlessly tomorrow.









